Businesses are ditching traditional keys and looking for smarter ways to control access to their spaces. Most people assume keyless entry is just about convenience and getting rid of metal keys. Yet what really stands out is how keyless entry can grant or revoke access in milliseconds and generate complete access logs for every door. That level of control and security is changing how companies think about safety and efficiency.
Table of Contents
- What Is Keyless Entry And How Does It Work?
- Why Keyless Entry Matters For Your Business
- Key Components Of Keyless Entry Systems
- Real-World Applications Of Keyless Entry In Businesses
- The Future Of Keyless Entry In Commercial Security
Quick Summary
| Takeaway | Explanation |
|---|---|
| Keyless entry enhances security and convenience | It replaces physical keys with digital methods, providing better access control and efficiency. |
| Instant access revocation is possible | Administrators can immediately disable access for lost credentials or terminated employees, enhancing safety. |
| Detailed access logs support security audits | Keyless entry systems log each entry and exit, allowing businesses to monitor and analyze access patterns effectively. |
| Operational efficiency reduces management costs | Eliminating physical key management decreases administrative tasks and leads to cost savings for the organization. |
| Future technologies will integrate AI and biometrics | Upcoming systems will combine advanced authentication methods, improving security through real-time data and intelligence. |
What is Keyless Entry and How Does It Work?
Keyless entry represents a modern security solution transforming how businesses control and manage access to their premises. Unlike traditional lock and key systems, keyless entry utilizes advanced technological mechanisms that eliminate physical keys while providing enhanced security and convenience.
Below is a breakdown of the main identification methods used in keyless entry systems, summarizing how each works along with their key advantages.
| Identification Method | How It Works | Key Advantages |
|---|---|---|
| Proximity Cards | Card is brought near a reader, sending data electronically | Fast entry, contactless operation |
| Biometric Scanners | Scans unique features such as fingerprints or face | Hard to duplicate, high security |
| Numerical Keypads | User enters a numeric code for verification | No need for physical device, flexible credential |
The Core Technology Behind Keyless Entry
At its foundation, keyless entry systems operate through electronic authentication methods. These systems replace mechanical locks with sophisticated digital interfaces that recognize authorized personnel through various identification techniques. Learn more about our keyless entry solutions that can revolutionize your business security.
The primary identification methods include:
- Proximity Cards: Small electronic cards that communicate with a reader when brought close to the access point
- Biometric Scanners: Using unique personal characteristics like fingerprints or facial recognition
- Numerical Keypads: Requiring a specific numeric code for entry
Authentication and Access Control Mechanics
When an authorized user approaches an entry point, the keyless system performs a rapid verification process. According to Cybersecurity and Infrastructure Security Agency, these systems validate credentials through encrypted communication between the identification method and the central access control unit.
The authentication typically involves matching the presented credentials against a pre-registered database of authorized personnel. Successful verification triggers electronic locks, granting seamless entry without physical key manipulation. This process occurs within milliseconds, providing both security and efficiency.
Keyless entry systems also generate detailed access logs, tracking every entry and exit. This feature enables businesses to monitor and audit access patterns, enhancing overall security management and providing valuable insights into facility usage.
Why Keyless Entry Matters for Your Business
Businesses today face increasingly complex security challenges that demand sophisticated solutions. Keyless entry systems offer a comprehensive approach to managing access, protecting assets, and streamlining operational efficiency. Read more about our keyless entry advantages and transform your business security strategy.
Enhanced Security and Control
Traditional key systems present significant vulnerabilities that keyless entry effectively mitigates. According to National Security Research Institute, physical keys can be duplicated, lost, or stolen, creating substantial security risks. Keyless entry systems eliminate these concerns through advanced authentication methods.
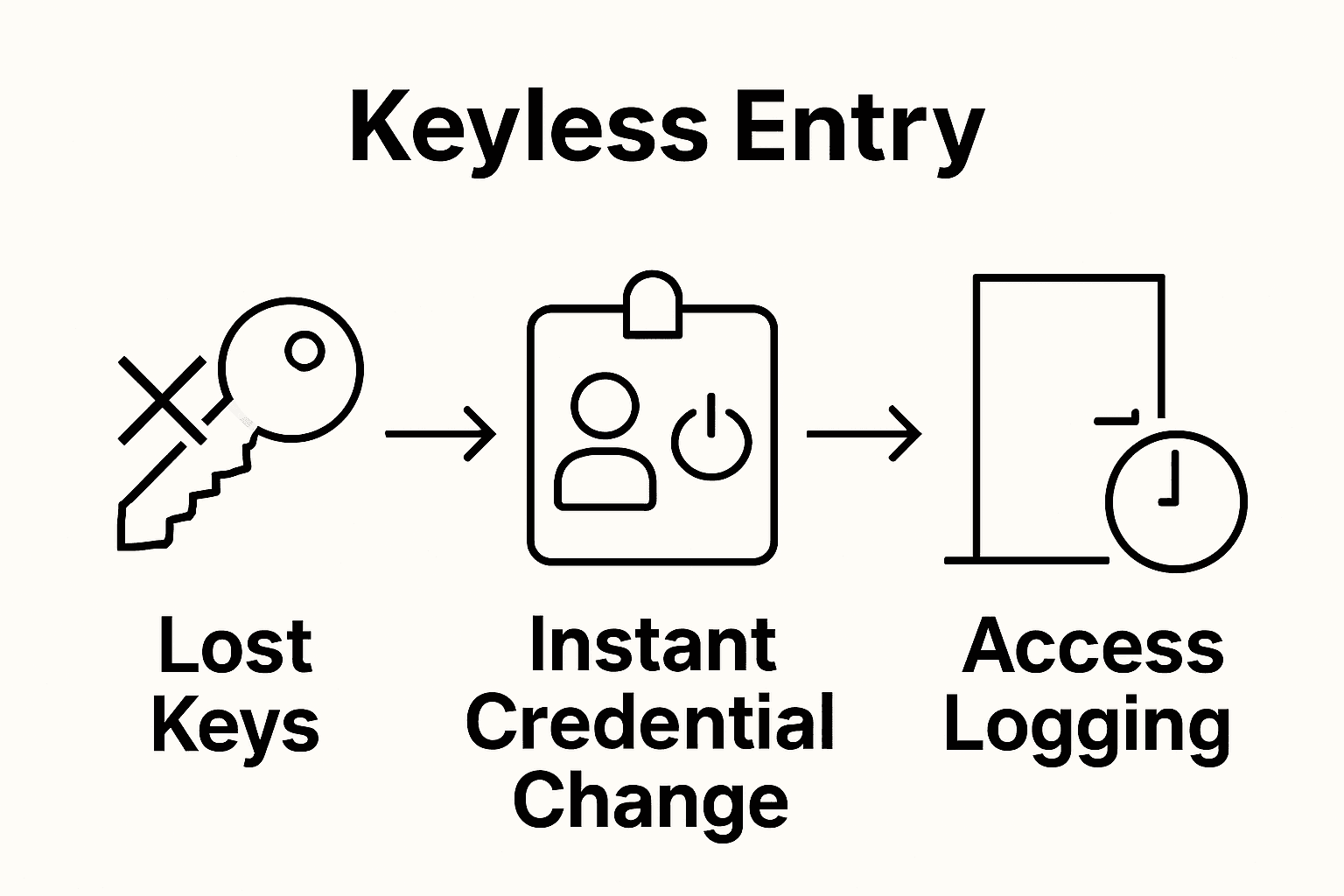
Key security improvements include:
- Instant Credential Revocation: Immediately disable access for terminated employees or lost credentials
- Detailed Access Logs: Track and monitor every entry and exit precisely
- Multi Level Access Permissions: Create granular access controls for different employee roles
Operational Efficiency and Cost Savings
Beyond security, keyless entry systems significantly enhance business operational efficiency. The elimination of physical key management reduces administrative overhead and associated costs. Businesses no longer need to manage complex key distribution, replacement, and tracking processes.
The integration of keyless entry with modern workplace technologies enables seamless access management. Automated systems reduce human error, minimize security breaches, and provide real time monitoring capabilities. These technological advantages translate directly into operational cost savings and improved workplace productivity.
Key Components of Keyless Entry Systems
Keyless entry systems are complex technological ecosystems comprising multiple interconnected components that work together to provide secure, efficient access management. Learn more about our comprehensive keyless entry solutions that integrate cutting edge technology and robust security protocols.
Electronic Access Control Hardware
The physical infrastructure of keyless entry systems consists of several critical hardware elements. According to National Institute of Standards and Technology, these components form the foundational architecture of modern access management solutions.
Key hardware components include:
- Access Readers: Electronic devices that scan and authenticate credentials
- Electronic Locks: Mechanisms that engage or disengage based on verified access signals
- Control Panels: Central units managing communication between readers and locks
Authentication and Communication Technologies
At the heart of keyless entry systems are sophisticated authentication mechanisms that validate user credentials. These systems use encrypted communication protocols to ensure secure data transmission between different system components. The authentication process involves multiple layers of verification, including credential matching, permission validation, and real time access logging.
Modern keyless entry systems leverage advanced communication technologies like radio frequency identification (RFID), near field communication (NFC), and cloud based management platforms. These technologies enable flexible, scalable access control solutions that can be remotely managed and updated in real time.
Real-World Applications of Keyless Entry in Businesses
Keyless entry systems have transcended traditional security paradigms, becoming integral solutions across diverse business environments.
This table summarizes how different industries implement keyless entry systems and the specific security needs each industry addresses.
| Industry | Keyless Entry Application | Security Needs Addressed |
|---|---|---|
| Healthcare Facilities | Restricting sensitive area access, patient record protection | Confidentiality and privacy |
| Corporate Offices | Multi-level permissions for employees and visitors | Segregated access, visitor management |
| Research Laboratories | Controlling access to high-security zones, IP protection | IP safeguarding, restricted zone control |
| Explore our comprehensive commercial lock solutions to understand the versatility of modern access control technologies. |
Industry-Specific Implementations
Different business sectors leverage keyless entry systems uniquely to address their specific security requirements. According to Security Industry Association, the adaptability of these systems makes them invaluable across multiple professional contexts.
Key industry applications include:
- Healthcare Facilities: Restricting sensitive area access and maintaining patient confidentiality
- Corporate Offices: Managing multi-level access permissions for employees and visitors
- Research Laboratories: Protecting intellectual property and controlling high-security zones
Scalable Security Solutions
Modern keyless entry systems offer unprecedented flexibility for businesses of all sizes. Small startups and large enterprises can implement customized access control strategies that grow with their organizational needs. The technological infrastructure allows for seamless integration with existing security protocols, enabling businesses to enhance their protective measures without complete system overhauls.
These systems provide granular control mechanisms that go beyond traditional security approaches. Administrators can create dynamic access profiles, set time-based permissions, and instantly modify access rights across entire organizational networks.
 The result is a responsive, intelligent security ecosystem that adapts to changing business requirements while maintaining robust protection.
The result is a responsive, intelligent security ecosystem that adapts to changing business requirements while maintaining robust protection.
The Future of Keyless Entry in Commercial Security
The commercial security landscape is rapidly evolving, with keyless entry systems at the forefront of technological innovation. These advanced solutions are transforming how businesses approach access control, security management, and operational efficiency. The next generation of keyless entry technologies promises unprecedented levels of integration, intelligence, and adaptive protection.
Emerging Authentication Technologies
Future keyless entry systems will move beyond traditional credential verification methods. Advanced authentication standards are introducing multi-factor authentication mechanisms that significantly enhance security protocols. These technologies combine multiple verification layers to create more robust access control environments.
Emerging authentication approaches include:
- Biometric Integration: Combining fingerprint, facial recognition, and behavioral pattern analysis
- AI Powered Threat Detection: Real time anomaly identification and risk assessment
- Blockchain Credential Verification: Decentralized, tamper proof authentication systems
Intelligent Security Ecosystems
Keyless entry systems are evolving from standalone security tools to comprehensive, interconnected intelligent platforms. Modern systems will seamlessly integrate with broader organizational technology infrastructures, enabling dynamic, context aware access management. Businesses will gain unprecedented visibility and control over their physical and digital security landscapes.
This integration will allow for sophisticated permission management, where access rights can be automatically adjusted based on real time contextual information such as employee roles, time of day, organizational changes, and potential security risks. The result will be a more responsive, adaptive security approach that anticipates and mitigates potential vulnerabilities before they can be exploited.
Elevate Your Business Security with Trusted Keyless Entry Solutions
Are you overwhelmed by the risks and hassles of traditional keys as detailed in our comprehensive guide? Lost keys, unauthorized duplication, and outdated systems can create headaches and leave your business vulnerable. Now is the time to take control of your access management with a proven local provider that understands how essential reliability and rapid support are for Greater Toronto Area businesses. Explore how our expert locksmith services empower you to move beyond these security challenges with advanced keyless entry technology.
When security and convenience matter most, let us show you how to achieve instant credential revocation, detailed access logs, and scalable solutions tailored to your workplace. Visit My Locksmiths now for immediate help or to start your business upgrade. Our experienced technicians are ready to support your transition to keyless access. Strengthen your security and simplify your operations today. For more options and information, head to our services page.
Frequently Asked Questions
What is a keyless entry system?
Keyless entry systems are modern security solutions that replace traditional lock-and-key systems with electronic authentication methods, enhancing security and convenience for businesses.
How do keyless entry systems work?
Keyless entry systems work by using electronic mechanisms to authenticate users through methods like proximity cards, biometric scanners, or numerical keypads, allowing for seamless entry without physical keys.
What are the advantages of using keyless entry for businesses?
Keyless entry offers enhanced security, operational efficiency, instant credential revocation, detailed access logs, and customizable access permissions, making it a valuable security solution for businesses.
Can keyless entry systems track access activity?
Yes, keyless entry systems generate detailed access logs that track every entry and exit, allowing businesses to monitor and audit access patterns for improved security management.







