Every day, confidential data, valuable equipment, and even personal safety depend on the strength of access controls. Research shows that unauthorized entry is one of the top causes of corporate security breaches worldwide. As organizations grow and security threats evolve, understanding what defines a restricted area—and exactly how access should be managed—becomes critical. This guide unpacks the principles of restricted area access, giving you clear insights into the systems, regulations, and best practices that help protect what matters most.
Table of Contents
- Defining Restricted Area Access And Key Concepts
- Common Types Of Restricted Access Zones
- How Electronic And Physical Access Control Works
- Legal Regulations And Compliance In The Gta
- Risks, Liabilities, And Best Practices
Key Takeaways
| Point | Details |
|---|---|
| Restricted Area Definition | Restricted areas are controlled spaces with limited access, originally from military contexts, now prevalent in various sectors to protect valuable assets and information. |
| Access Management Components | Effective restricted access management includes authorization levels, verification mechanisms, monitoring systems, and physical barriers to ensure security. |
| Legal Compliance Considerations | Organizations must navigate legal regulations prioritizing safety and privacy, ensuring access management aligns with occupational health standards and specific industry requirements. |
| Risk Mitigation Strategies | Implementing comprehensive security measures, regular training, and clear documentation are crucial for reducing potential liabilities associated with restricted area access. |
Defining Restricted Area Access and Key Concepts
A restricted area represents a controlled space where entry is limited exclusively to individuals with specific authorization. According to Merriam-Webster, this term originally emerged from military contexts, describing zones where personnel are excluded unless specially permitted for security purposes.
In modern security frameworks, restricted areas extend far beyond military installations. Wikipedia highlights that these spaces can encompass diverse environments like airport security zones, specialized industrial facilities, research laboratories, and sensitive corporate spaces. The core principle remains consistent: controlled access protecting valuable assets, confidential information, or potentially hazardous environments.
Restricted area access management involves several critical components:
- Authorization Levels: Defining precise permissions for different personnel
- Access Verification: Implementing mechanisms to confirm individual credentials
- Monitoring Systems: Tracking and recording all entry and exit activities
- Physical Barriers: Using technological and architectural constraints
Understanding these key concepts is crucial for organizations seeking robust security strategies. Understanding Access Control Systems for Better Security offers deeper insights into implementing comprehensive access management protocols that protect your most valuable resources.
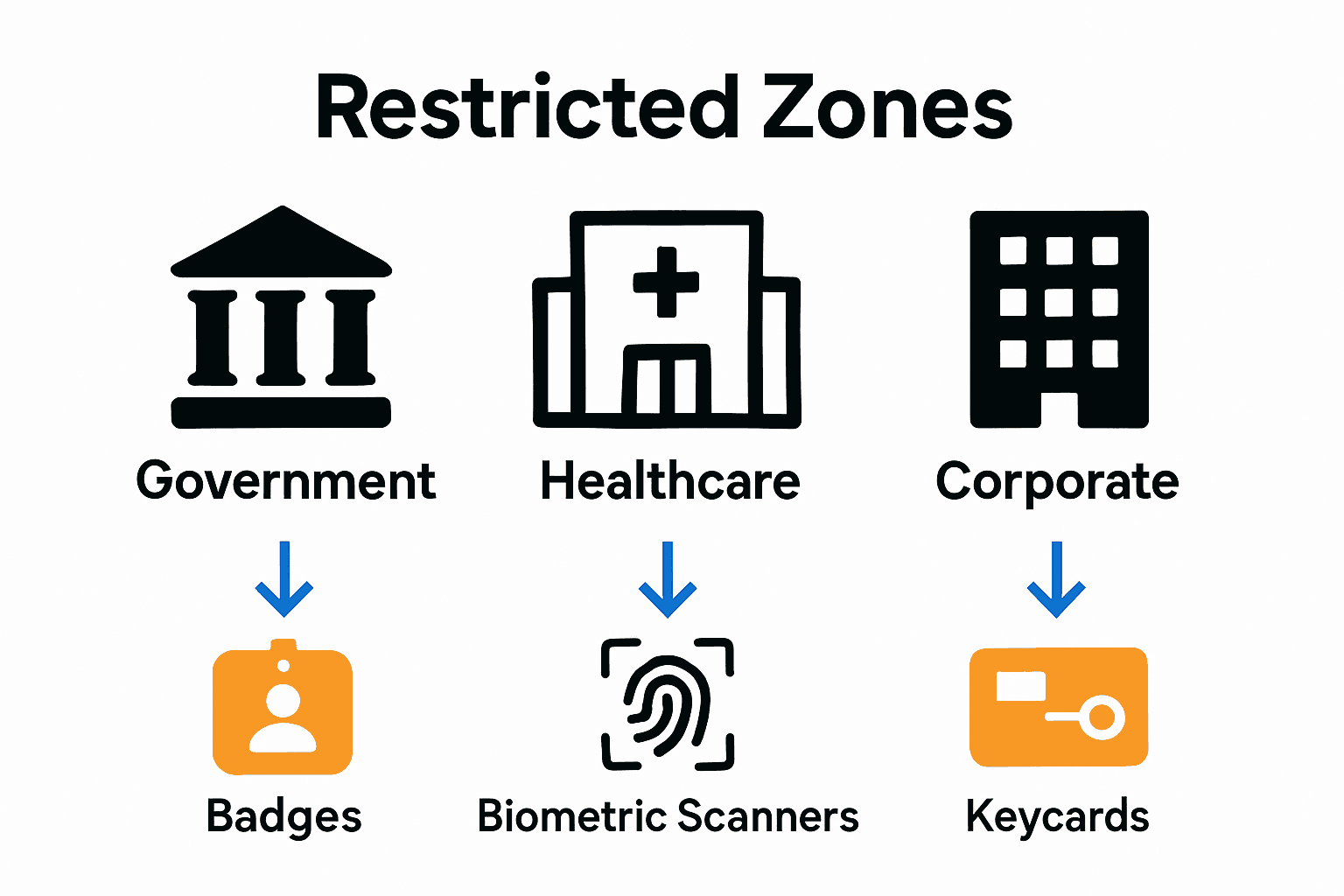
Common Types of Restricted Access Zones
Restricted access zones vary significantly across different industries and sectors, each designed to protect specific assets, information, or environments. Wikipedia highlights how military zones represent the most stringent form of restricted access, characterized by comprehensive security measures that legally prevent unauthorized entry and protect sensitive national infrastructure.
Beyond military contexts, restricted access zones emerge in diverse professional settings. Wikipedia reveals specialized environments like pharmaceutical and electronics manufacturing, which utilize restricted-access barrier systems (RABS) to create physical separations between workers and critical production areas. These controlled environments ensure product integrity, prevent contamination, and maintain extremely high safety standards.

Key types of restricted access zones include:
Here’s a comparison of common restricted access zones and their key security needs:
| Zone Type | Main Assets Protected | Typical Access Measures |
|---|---|---|
| Government Facilities | Classified documents Personnel safety | ID badges Armed security Surveillance cameras |
| Healthcare Settings | Patient information Medical supplies | Biometric readers Keycards Access logs |
| Industrial Zones | Equipment Hazardous materials | Restricted badges Barriers Environmental monitoring |
| Corporate Environments | Financial data Intellectual property | PIN codes Electronic locks Visitor logs |
| Research Institutions | Experimental data Specialized equipment | Secure entry points Video monitoring |
- Government Facilities: Secure administrative buildings, sensitive research centers
- Healthcare Settings: Surgical wings, medical research laboratories, pharmaceutical storage
- Industrial Zones: Manufacturing clean rooms, hazardous material storage, sensitive equipment areas
- Corporate Environments: Executive floors, server rooms, confidential document storage
- Research Institutions: High-security laboratories, specialized research zones
For organizations seeking to implement robust security protocols, top commercial door lock types can provide essential insights into creating effective access control mechanisms tailored to specific restricted zone requirements.
How Electronic and Physical Access Control Works
Wikipedia defines access control as a sophisticated system selectively restricting entry to specific places or resources, combining both physical and electronic security measures. At its core, this approach ensures that only authorized individuals can enter designated spaces, protecting valuable assets and maintaining organizational security.
Electronic access control technologies have revolutionized security mechanisms. Research from arXiv highlights emerging technologies like Radio Frequency Identification (RFID), which enables precise authentication by granting access exclusively to verified individuals. These systems go far beyond traditional lock and key approaches, offering real-time tracking, detailed access logs, and instantaneous security management.
Key components of comprehensive access control systems include:
Authentication Mechanisms:
- Keycards
- Biometric scanners
- PIN codes
- Proximity badges
Physical Barriers:
- Electronic locks
- Turnstiles
- Security gates
- Reinforced entry points
Monitoring Technologies:
- Real-time surveillance
- Access log recording
- Remote management capabilities
For businesses looking to upgrade their security infrastructure, keyless entry systems provide cutting-edge solutions that integrate seamlessly with modern access control technologies, offering enhanced protection and operational flexibility.
Legal Regulations and Compliance in the GTA
Restricted area access in the Greater Toronto Area involves complex legal frameworks that prioritize safety, privacy, and organizational security. Toronto Metropolitan University emphasizes the critical importance of strict authorization protocols, highlighting that accessing restricted spaces requires more than just physical entry control – it demands comprehensive training and adherence to specific safety procedures.
The legal landscape for restricted area management encompasses multiple regulatory dimensions. Organizations must navigate intricate requirements that balance security needs with individual rights, ensuring that access control mechanisms comply with provincial occupational health and safety regulations, privacy legislation, and industry-specific standards. Authorization levels become crucial, with different sectors requiring unique approaches to managing restricted zones.
Key legal compliance considerations include:
Workplace Safety Regulations:
- Mandatory safety training
- Risk assessment documentation
- Emergency access protocols
- Comprehensive incident reporting
Privacy Protection:
- Consent requirements for access monitoring
- Data collection limitations
- Secure information management
- Employee rights preservation
Industry-Specific Requirements:
- Healthcare confidentiality standards
- Financial sector security protocols
- Government facility access restrictions
- Technology sector intellectual property protection
Businesses seeking to navigate these complex requirements can benefit from understanding ADA compliant locks, which provide a foundational approach to creating accessible yet secure environments that meet legal standards.
Risks, Liabilities, and Best Practices
Restricted area security involves navigating a complex landscape of potential risks and legal vulnerabilities. University of Reading emphasizes the critical importance of clear identification and controlled entry points as fundamental strategies for mitigating organizational risks, highlighting that proper signage and access management can significantly reduce potential security breaches.
Understanding potential liabilities is crucial for organizations seeking to protect their assets and personnel. Organizational risk encompasses multiple dimensions, including financial exposure, potential legal challenges, and reputational damage that can arise from inadequate access control mechanisms. Zaun Ltd underscores the importance of implementing comprehensive security strategies that balance accessibility with robust protective measures.
Key risk mitigation strategies include:
Physical Security Measures:
- Comprehensive perimeter control
- Multi-layered access points
- Regular security infrastructure assessments
- Strategic barrier implementations
Liability Reduction Tactics:
- Detailed documentation of access protocols
- Regular staff training programs
- Incident response planning
- Clear communication of restricted zone boundaries
Technological Safeguards:
- Advanced authentication systems
- Real-time monitoring capabilities
- Automated access logging
- Rapid response detection mechanisms
Businesses looking to enhance their security frameworks can gain valuable insights by understanding ADA compliant locks, which provide a foundational approach to creating secure and accessible environments that minimize potential legal and operational risks.
Secure Your Restricted Areas with Trusted Locksmith Solutions
Managing restricted area access in the GTA requires precision, control, and trust. This guide highlights the critical need for proper authorization levels, advanced access verification, and reliable physical barriers to protect your valuable assets and sensitive environments. If you are facing challenges with maintaining strict security or upgrading to modern electronic access control, it is essential to partner with professionals who understand these complexities and can offer tailored solutions.
At My Locksmiths, we specialize in delivering fast, affordable, and dependable locksmith services across Greater Toronto. Whether you need high-security lock installations, advanced keyless entry systems, or expert repair and rekeying, our licensed technicians have the expertise to help you safeguard your restricted spaces effectively. Don’t risk security breaches or compliance issues. Act now to enhance protection with trusted locksmith solutions.
Protect your business or facility today by contacting My Locksmiths for a free consultation. Explore our comprehensive keyless entry systems and learn how you can implement state-of-the-art access control that matches the stringent requirements discussed in this guide. Take control of your restricted areas with confidence and expert support.
Frequently Asked Questions
What is a restricted area?
A restricted area is a controlled space where entry is limited to individuals with specific authorization, often to protect valuable assets, confidential information, or hazardous environments.
What are the key components of restricted area access management?
Key components include authorization levels, access verification mechanisms, monitoring systems, and physical barriers that ensure only authorized individuals can enter.
How do electronic access control systems work?
Electronic access control systems utilize technologies like RFID, keycards, biometric scanners, and electronic locks to restrict entry and monitor access, enhancing security and providing detailed access logs.
What are common security measures for various restricted access zones?
Common security measures include ID badges, biometric readers, surveillance cameras, electronic locks, and environmental monitoring, tailored to protect assets in government, healthcare, industrial, corporate, and research environments.







